Audit Policy
Windows Security EventLog is based on Audit Policy of Security Policy. There are 9 categories in Windows XP/2003. Since Vista, on the other hand, there are over 50 categories.
Default audit policy is disabled at XP, but is enabled with some categories at Vista or later. The command named auditpol(audituser) can read these condition when target is online. If you want to get all of audit policy settings, then run the following command:
> auditpol /get /category:*
Below is the sample screenshot of "HKLM\Security\Policy\PolAdtEv" value of Windows 10.
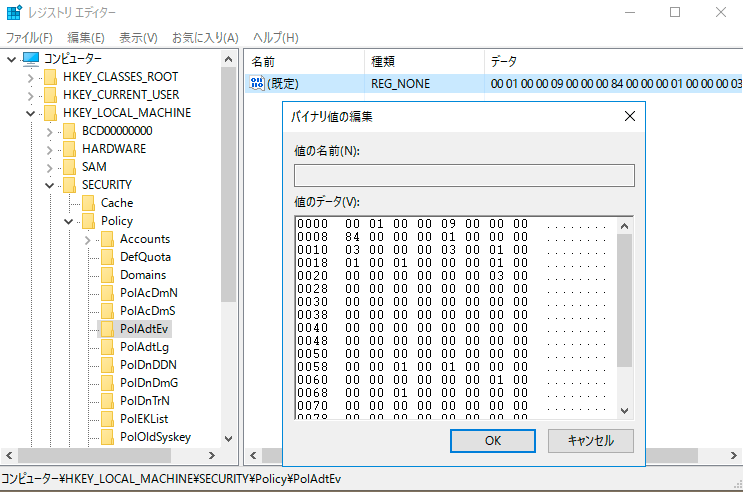
PolAdtEv Structure (prior to Vista)
Following is the information about PolAdtEv in Windows NT 4.0
How To Determine Audit Policies from the Registry
http://support.microsoft.com/kb/246120
In NT 4.0, there are only 7 categories. It differs from XP/2003 which have 9 categories. Book "EnCE Study Guide" by Steve Bunting or "Windows Forensic Analysis" by Steve Bunting introduce structure of PolAdtEv value.
PolAdtEv Structure (Vista or later)
I looked at the structure of PolAdtEv key
Download
PolAdtEv_Structure_en_rev5.pdf
Reference
PolAdtEv Parser
https://www.kazamiya.net/en/PolAdtEvParser
RegRipper - auditpol
https://github.com/keydet89/RegRipper2.8/blob/master/plugins/auditpol.pl
Volatility - auditpol
https://github.com/volatilityfoundation/volatility/blob/master/volatility/plugins/registry/auditpol.py
DIGITAL FORENSICS – SUPERTIMELINE & EVENT LOGS – PART I
https://countuponsecurity.com/2015/11/23/digital-forensics-supertimeline-event-logs-part-i/
History
2024-09-16
No changes for Windows 11 23H2, Windows Server 2022. Current revision is rev5.
2017-01-29
Updated for Windows 10(1607) and Windows Server 2016. Current revision is rev4.
2015-03-29
This title of content is changed, I have updated to support Windows 8.1/2012/10/Threshold and uploaded as rev3.
2010-08-08
The PDF is divided into (1)Windows 7/2008 (x64) and (2)Windows 2008(x32)/Vista. (1) includes "Detailed File Share" of "Object Access" category, but (2) does not include.