EvtxECmd, which has been developed by Eric Zimmerman provides us with better handling of Windows Event Log. I have confirmed it's capable of parsing evtx data which is carved by Bulk Extractor with Record Carving.
Here is my record what I have attempted.
- Verification Environment
Windows 10 x64 1903
Autopsy 4.11.0
Arsenal Image Mounter 2.6.40
ShadowExplorer 0.9
bulk_extractor-rec03
EvtxExplorer / EvtxECmd 0.4.3.0
LibreOffice 6.2.3 - Sample Image
FileServer_Disk0.e01 (available at Defcon DFIR CTF 2018 - Image 2)
To distinguish between existing and deleted event log records, I have extracted existing evtx files from disk image and vss snapshot at first. Then I have carved evtx chunks in unallocated space and reconstructed evtx. More details are as follows:
Extract evtx files from allocated and vss
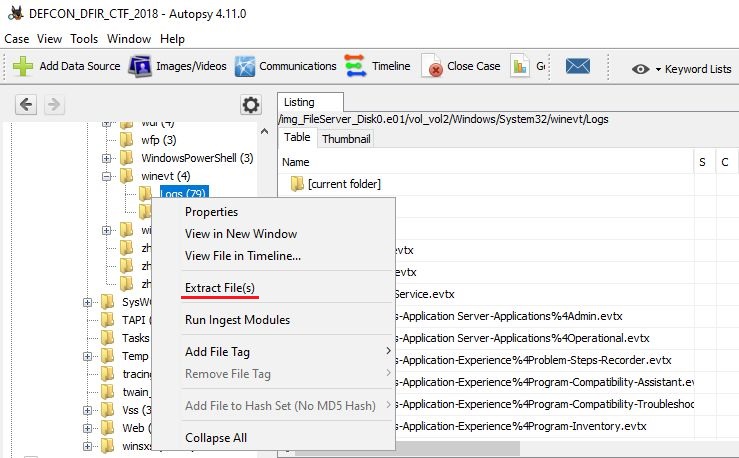
On Autopsy, create a new case and open image file named "FileServer_Disk0.e01". Move on to vol2 > Windows > System32 > winevt > Logs, right-click and choose "Extract File(s)".
Extracted files saved to "D:\DEFCON_DFIR_CTF_2018\Export\evtx" folder.
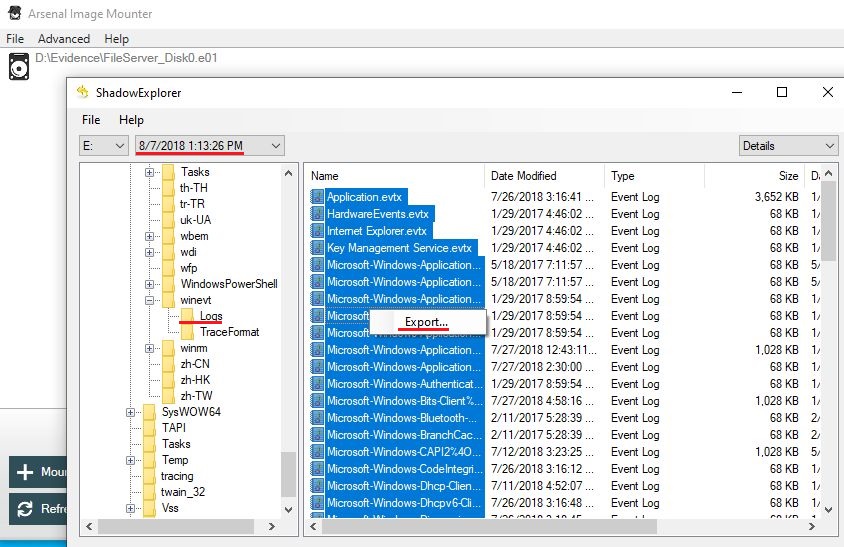
To extract evtx files from vss snapshot, mount "FileServer_Disk0.e01" using Arsenal Image Mounter then extract files into "D:\DEFCON_DFIR_CTF_2018\Export\vss_evtx" folder from a snapshot using ShadowExplorer.
Extract unallocated space into one file
On Autopsy, move on to vol2, right-click and choose "Extract Unallocated Space to Single File".
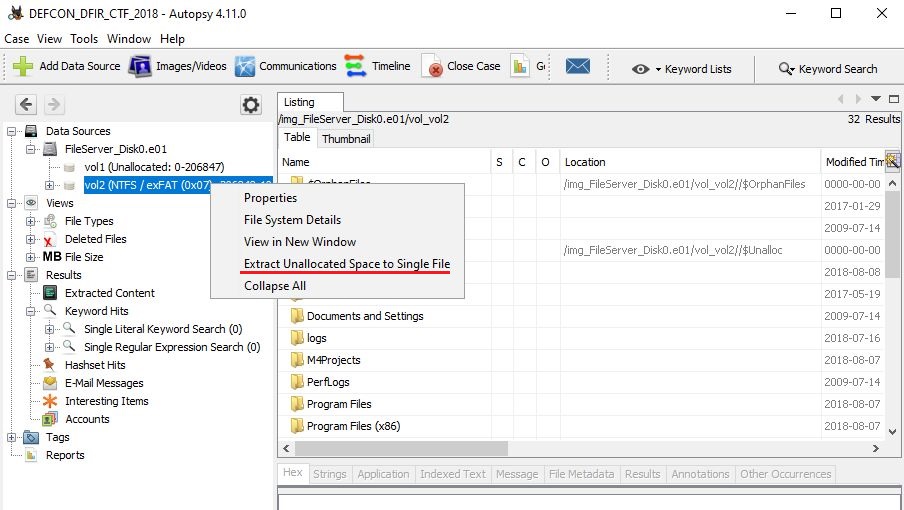
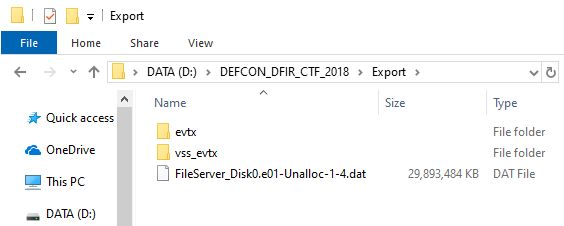
Extracted file saved to "D:\DEFCON_DFIR_CTF_2018\Export" folder. The data are as follows so far:
Carve evtx chunks and reconstruct evtx files using bulk_extractor-rec
Bulk Extractor with Record Carving (bulk_extractor-rec03) has a plugin for evtx. The plugin looks for evtx header, chunk and record. If it finds orphan chunk data, generates corresponding header then saves as evtx file. Details please refer to p.25-31 of my slide.
A command to carve evtx data looks like:
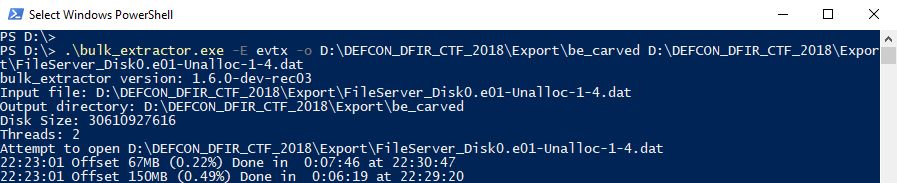
bulk_extractor.exe -E evtx -o output_directory input_file
The following figure shows carving evtx data from "FileServer_Disk0.e01-Unalloc-1-4.dat", which is a file means unallocated space.
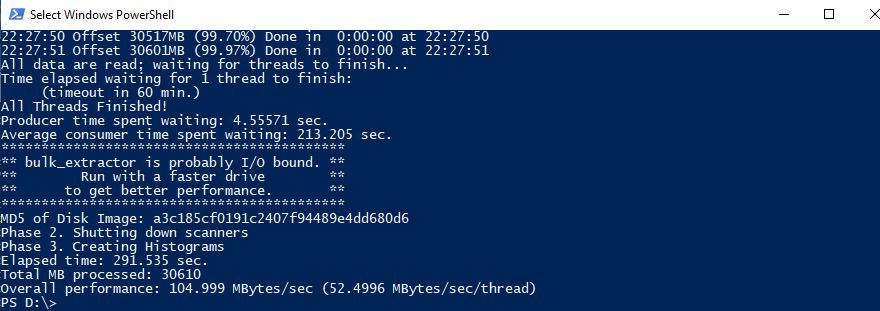
Carved data are placed in "evtx_carved" folder under specified -o option "D:\DEFCON_DFIR_CTF_2018\Export\be_carved".
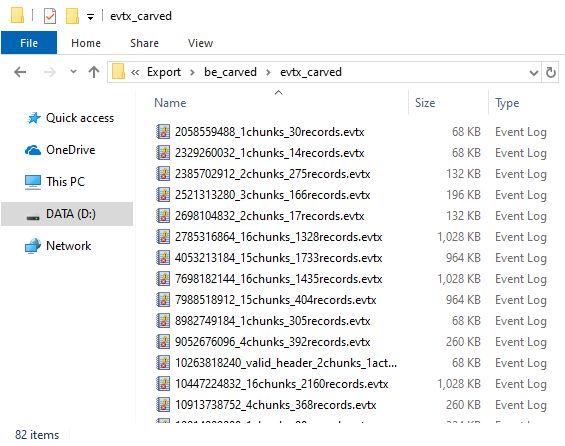
The number of recovered files is 82.
Parse evtx files using EvtxECmd
Now it's time for EvtxECmd. EvtxECmd supports -d option, which is able to parse multiple files at one time. To check whether unique deleted records exist, run EvtxECmd command for evtx, vss_evtx and evtx_carved folder respectively.
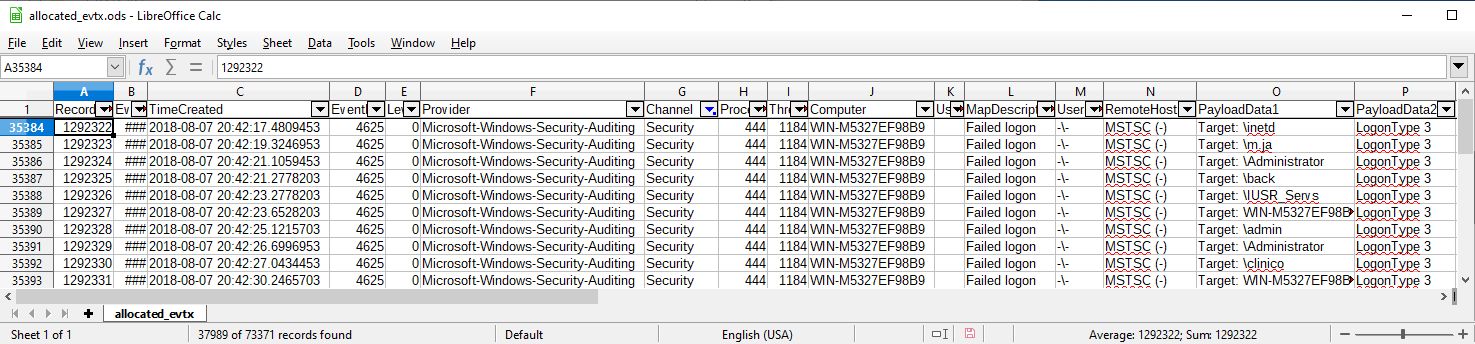
EvtxECmd.exe -d "D:\DEFCON_DFIR_CTF_2018\Export\evtx" --csv D:\ --csvf allocated_evtx.csv
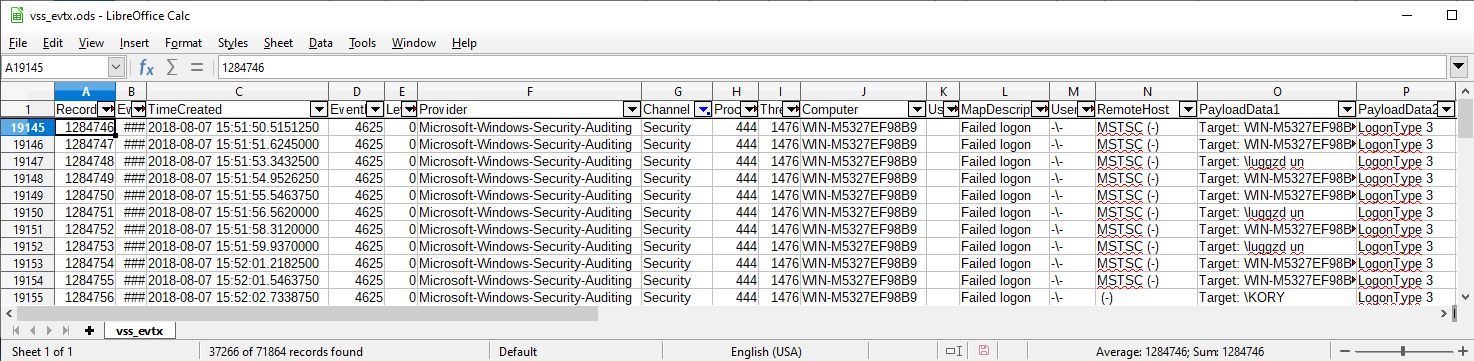
EvtxECmd.exe -d "D:\DEFCON_DFIR_CTF_2018\Export\vss_evtx" --csv D:\ --csvf allocated_evtx.csv
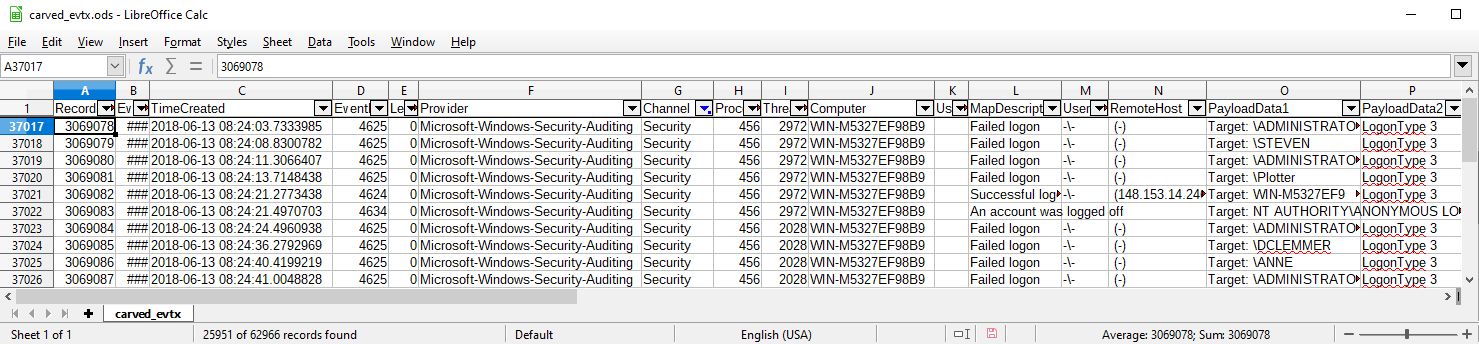
EvtxECmd.exe -d "D:\DEFCON_DFIR_CTF_2018\Export\be_carved\evtx_carved" --csv D:\ --csvf allocated_evtx.csv
The following figures show when I ran EvtxECmd for "evtx_carved" folder:
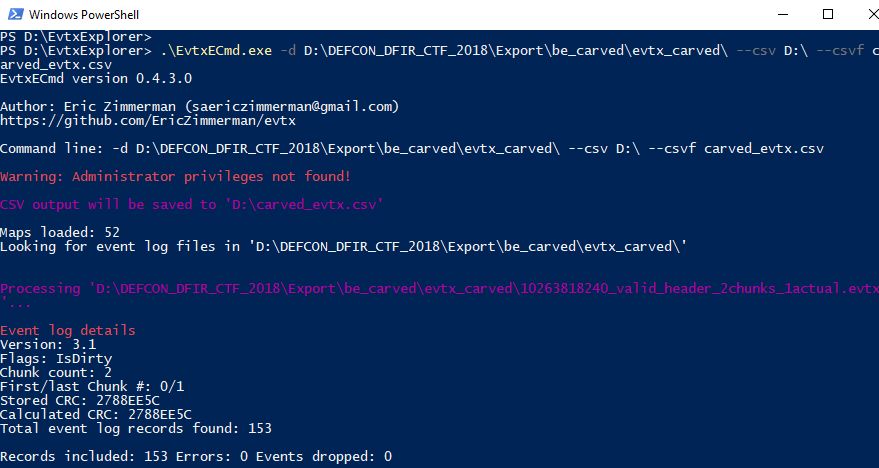
EvtxECmd processed 77 files with some errors. However, I have confirmed Event Viewer or Log Parser failed to read some of these files so EvtxECmd produces better results.
Check the result
Open csv files with LibreOffice. The following figures show after sort by "TimeCreated" and filter "Security" by "Channel":
There are a lot of EventID 4625 records, mean "Failed logon". When I look at TimeGenerated column, we understand that we can recover previous records. According to RecordNumber column, the values of deleted records are larger than the values of allocated and vss. It seems that Security.evtx has been cleared at some point from 2018-06-13 to 2018-08-07.
Conclusion
Now we are getting better to handle deleted evtx records. Thank you, Eric!
By the way, I have confirmed EVTXtract has also carved evtx records. It may carve out more records than bulk_extractor-rec but output format is only XML. If you have to cope with event log thoroughly, I recommend that you try both bulk_extractor-rec and EVTXtract.